The 192-97 LT1 diagram, a foundational concept in network communication, provides a visual representation of the complex processes involved in transmitting data across a network. This diagram, often referred to as the “OSI Model,” Artikels the seven layers of network communication, each responsible for specific functions, and their interactions.
By understanding the 192-97 LT1 diagram, we can gain valuable insights into how data travels from a source to a destination, the protocols governing communication, and the underlying security considerations.
The 192-97 LT1 diagram’s significance lies in its ability to simplify a complex system, enabling network engineers and professionals to analyze, troubleshoot, and optimize network performance. It provides a common framework for understanding network communication, regardless of the specific technologies involved.
This diagram also plays a crucial role in network security, as it highlights potential vulnerabilities and helps identify appropriate security measures.
Introduction to 192-97 LT1 Diagram
The 192-97 LT1 diagram, also known as the “Layer 2 Tunneling Protocol (L2TP) over IPsec (IP Security Protocol)” diagram, is a critical component in the realm of network communication, particularly for establishing secure and reliable connections between geographically dispersed networks.
This diagram illustrates the intricate process of setting up a secure tunnel between two endpoints using L2TP and IPsec, ensuring the confidentiality and integrity of data transmitted across the network.The 192-97 LT1 diagram provides a comprehensive visual representation of the various steps involved in the L2TP/IPsec tunneling process.
It Artikels the communication flow between the different network components, including the client, server, and intermediate network devices, revealing the complex interplay of protocols and security measures. Understanding the diagram’s elements and their relationships is crucial for network administrators and security professionals seeking to implement and manage secure network connections.
Components and Relationships in the 192-97 LT1 Diagram
The 192-97 LT1 diagram comprises several key components, each playing a distinct role in establishing and maintaining a secure L2TP/IPsec tunnel. These components include:* Client:The device initiating the connection request, typically a user’s computer or mobile device.
Server
The device accepting the connection request and providing access to the network resources.
L2TP Control Connection
The initial connection established between the client and server, using the L2TP protocol, to negotiate the tunnel parameters and authenticate the devices.
IPsec Tunnel
The secure channel created between the client and server, using the IPsec protocol, for transmitting data securely.
IPsec Security Association (SA)
The set of parameters used to encrypt and authenticate data exchanged within the IPsec tunnel, ensuring confidentiality and integrity.
Network Address Translation (NAT)
A technique used to translate private IP addresses to public IP addresses, enabling devices behind a firewall to communicate with external networks.The relationships between these components are dynamic and evolve throughout the tunnel establishment process. The client initiates the connection by sending an L2TP control connection request to the server.
The server responds with an acknowledgment, and the L2TP control connection is established. Once the connection is authenticated, the client and server negotiate the parameters for the IPsec tunnel, including the encryption and authentication algorithms. Finally, the IPsec tunnel is established, and data transmission begins.
Understanding the Key Elements of the 192-97 LT1 Diagram
The 192-97 LT1 diagram is a visual representation of the intricate communication flow involved in establishing a secure L2TP/IPsec tunnel. It highlights the key elements and their relationships, providing a clear understanding of the process.* L2TP Control Connection:The initial connection established between the client and server, using the L2TP protocol, to negotiate the tunnel parameters and authenticate the devices.
This connection is responsible for setting up the tunnel and establishing the communication channel between the client and server.
IPsec Tunnel
The secure channel created between the client and server, using the IPsec protocol, for transmitting data securely. This tunnel encrypts and authenticates data, ensuring confidentiality and integrity.
IPsec Security Association (SA)
The set of parameters used to encrypt and authenticate data exchanged within the IPsec tunnel. The SA specifies the encryption algorithms, authentication mechanisms, and other security settings used to protect data transmission.
Network Address Translation (NAT)
A technique used to translate private IP addresses to public IP addresses, enabling devices behind a firewall to communicate with external networks. NAT is often employed in conjunction with L2TP/IPsec tunneling to facilitate communication between clients and servers located on different networks.
Importance of the 192-97 LT1 Diagram
The 192-97 LT1 diagram is a crucial tool for network administrators and security professionals, providing a visual representation of the L2TP/IPsec tunneling process. Understanding the diagram’s elements and their relationships is essential for:* Troubleshooting Network Issues:By visualizing the communication flow, administrators can identify potential bottlenecks or security vulnerabilities.
Implementing Secure Connections
The diagram provides a blueprint for configuring L2TP/IPsec tunnels, ensuring proper security settings and protocols are implemented.
Monitoring Network Performance
The diagram helps track data flow and identify any performance issues related to the tunnel.The 192-97 LT1 diagram serves as a valuable resource for understanding the complexities of L2TP/IPsec tunneling, enabling network administrators to implement secure and reliable connections across diverse network environments.
Network Layers and Protocols: 192-97 Lt1 Diagram
The 192-97 LT1 diagram depicts the interaction of various network layers and protocols involved in data transmission. Each layer performs a specific function, contributing to the overall communication process.
Network Layers in the 192-97 LT1 Diagram
The 192-97 LT1 diagram represents the communication process using the seven-layer Open Systems Interconnection (OSI) model. The OSI model provides a standardized framework for understanding network communication.
- Application Layer:This layer provides services to applications that use the network. Examples include email, web browsing, and file transfer protocols (FTP). The Application Layer interacts with user applications and ensures data is formatted and presented in a way that is understandable by the user.
In the 192-97 LT1 diagram, the Application Layer might be represented by a web browser or email client.
- Presentation Layer:This layer handles data formatting and encryption. It ensures data is presented in a way that is compatible with the receiving system. The Presentation Layer might be responsible for converting data from one format to another, such as converting text from ASCII to Unicode.
In the 192-97 LT1 diagram, the Presentation Layer might be represented by a security protocol like SSL/TLS.
- Session Layer:This layer manages communication sessions between applications. It establishes, coordinates, and terminates conversations between applications. The Session Layer might be responsible for managing the flow of data between two applications, ensuring that data is delivered in the correct order. In the 192-97 LT1 diagram, the Session Layer might be represented by a protocol that handles the establishment and termination of communication sessions, like TCP.
- Transport Layer:This layer provides reliable and efficient data transfer between applications. It ensures data is delivered without errors and in the correct order. The Transport Layer might be responsible for segmenting data into packets and reassembling them at the destination. It also handles error detection and retransmission.
In the 192-97 LT1 diagram, the Transport Layer might be represented by TCP or UDP.
- Network Layer:This layer handles routing and addressing. It determines the best path for data to travel from source to destination. The Network Layer might be responsible for assigning IP addresses to devices and determining the route that data should take to reach its destination.
In the 192-97 LT1 diagram, the Network Layer might be represented by the router, which forwards data packets based on their destination IP addresses.
- Data Link Layer:This layer provides error detection and correction for data transmission over physical links. It ensures data is transmitted without errors. The Data Link Layer might be responsible for detecting and correcting errors in data transmission. It might also be responsible for framing data into packets.
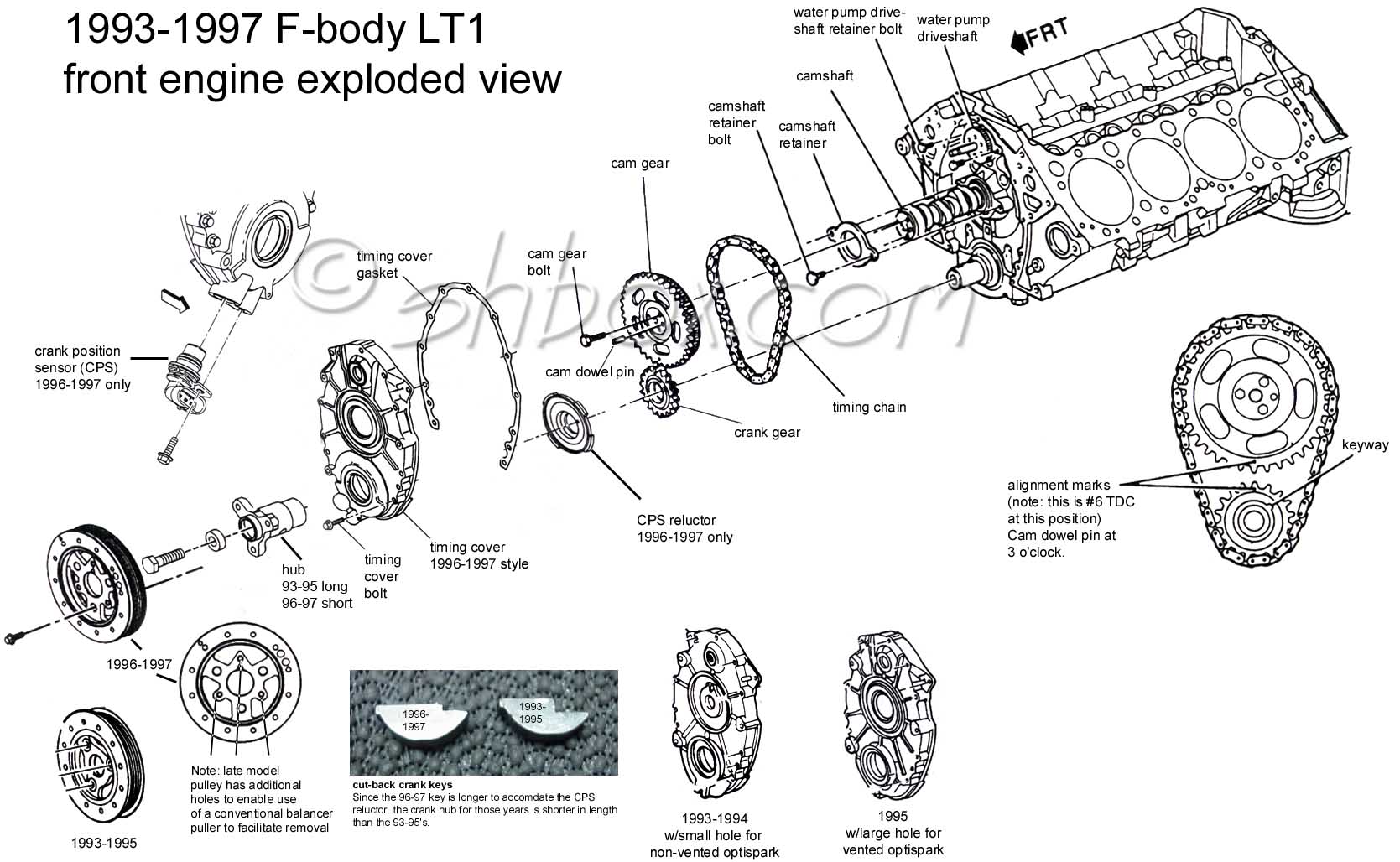
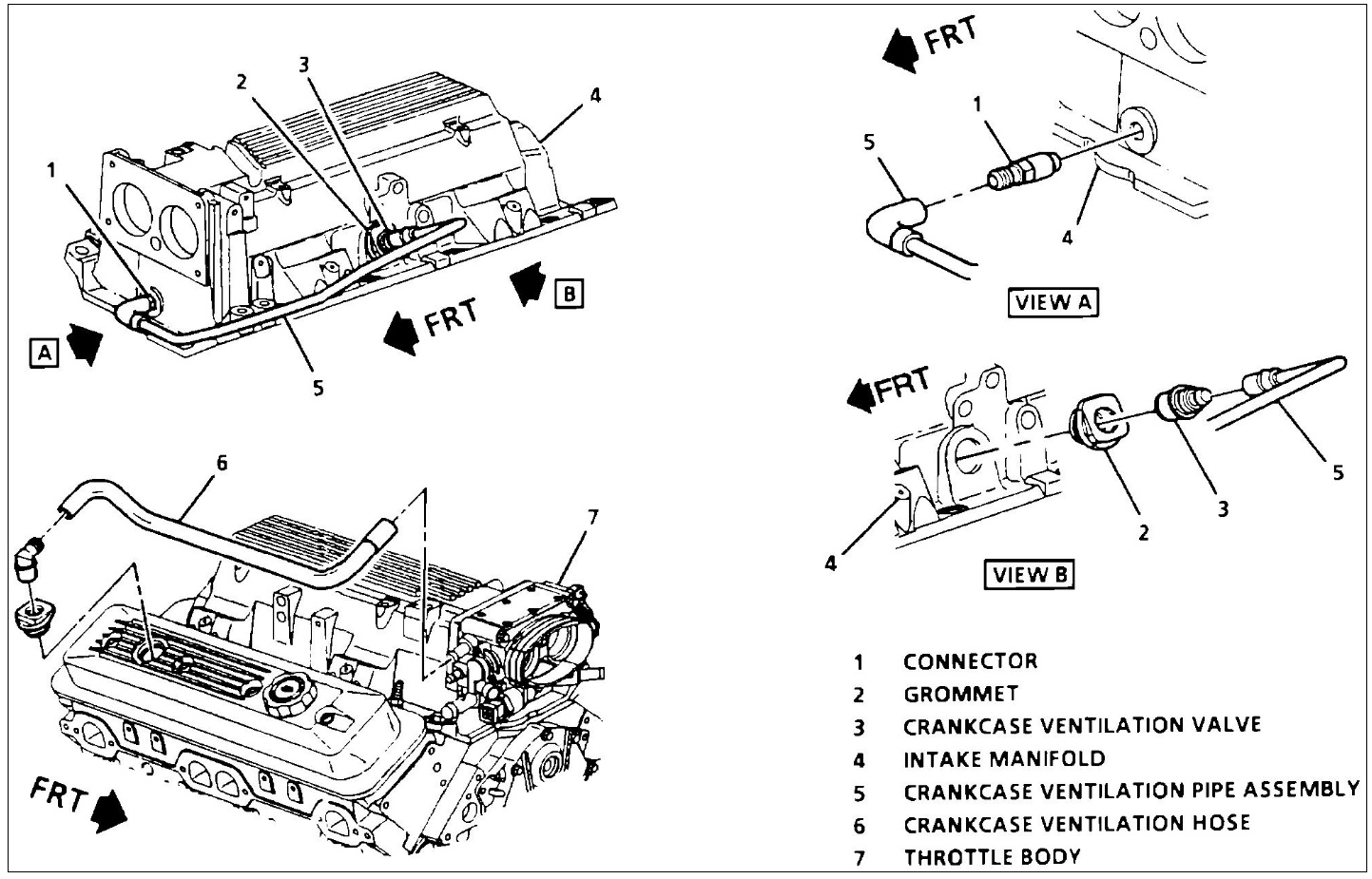
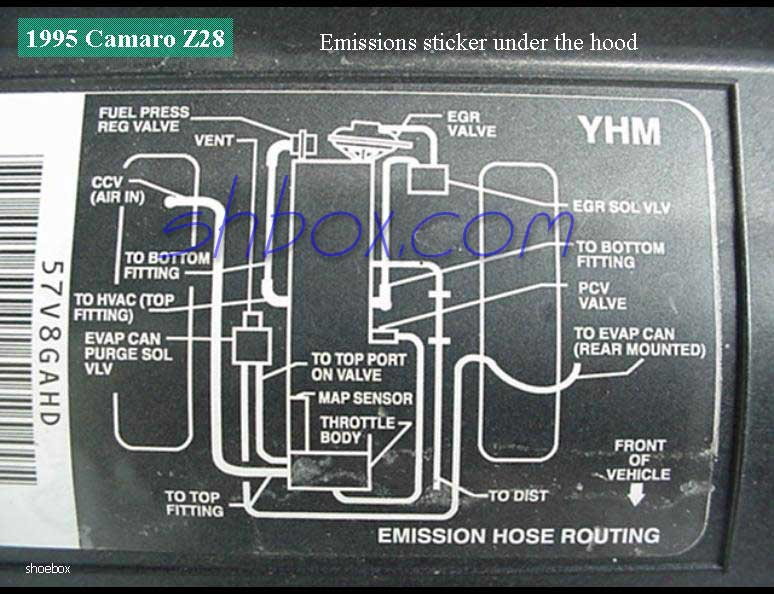
The 192-97 LT1 diagram, a roadmap of the engine’s inner workings, reveals a complex tapestry of hoses and lines. Understanding the flow of air and fuel through the system requires careful attention to detail, much like deciphering the intricate web of vacuum lines in a 2013 6.7 F250 vacuum system diagram.
Similarly, the LT1 diagram highlights the interplay of components like the throttle body, intake manifold, and fuel injectors, all contributing to the engine’s seamless operation.
In the 192-97 LT1 diagram, the Data Link Layer might be represented by a network interface card (NIC) or a switch, which handles data transmission between devices on the same network.
- Physical Layer:This layer defines the physical characteristics of the network, such as cables, connectors, and transmission signals. It handles the physical transmission of data over the network. The Physical Layer might be responsible for encoding and decoding data into electrical signals.
In the 192-97 LT1 diagram, the Physical Layer might be represented by the physical cable connecting devices on the network.
Protocols Associated with Network Layers
Each layer in the OSI model uses specific protocols to perform its functions.
- Application Layer:This layer utilizes protocols such as HTTP (Hypertext Transfer Protocol) for web browsing, SMTP (Simple Mail Transfer Protocol) for email, and FTP (File Transfer Protocol) for file transfer.
- Presentation Layer:This layer uses protocols like SSL/TLS (Secure Sockets Layer/Transport Layer Security) for encryption and data integrity. It ensures secure communication between applications.
- Session Layer:This layer uses protocols like RPC (Remote Procedure Call) and NetBIOS (Network Basic Input/Output System) to manage communication sessions between applications.
- Transport Layer:This layer utilizes protocols like TCP (Transmission Control Protocol) for reliable, connection-oriented data transfer and UDP (User Datagram Protocol) for faster, connectionless data transfer. TCP provides error checking and retransmission, while UDP prioritizes speed and efficiency.
- Network Layer:This layer uses protocols like IP (Internet Protocol) for addressing and routing data packets across the network. It enables communication between devices on different networks.
- Data Link Layer:This layer uses protocols like Ethernet for physical layer access and MAC (Media Access Control) addressing for identifying devices on a network. It also uses protocols like PPP (Point-to-Point Protocol) and SLIP (Serial Line Internet Protocol) for establishing communication over serial lines.
- Physical Layer:This layer utilizes standards such as RS-232, USB, and Ethernet for defining physical connections and transmission signals. It ensures data can be transmitted over the physical network medium.
Interaction Between Network Layers
Network layers work together in a hierarchical manner to facilitate data transmission. Each layer relies on the services provided by the lower layer and offers services to the upper layer.
- Data Encapsulation:Data is encapsulated as it moves from the Application Layer to the Physical Layer. Each layer adds its own header information to the data, creating a layered structure. The data is then transmitted through the network, with each layer removing its header information as the data moves up the stack.
- Protocol Interaction:Protocols at each layer interact to ensure seamless communication. For example, TCP at the Transport Layer uses IP at the Network Layer to route data packets. The Application Layer uses protocols like HTTP to access web pages, relying on lower layers for data transmission and delivery.
Addressing and Routing
The 192-97 LT1 diagram utilizes addressing schemes and routing protocols to facilitate efficient and reliable data transmission between network devices. Addressing enables unique identification of each device, while routing protocols determine the optimal paths for data flow.
Addressing Schemes
Addressing schemes provide a mechanism for identifying and locating devices within a network. In the 192-97 LT1 diagram, the most prevalent addressing scheme is Internet Protocol (IP) addressing. IP addresses are used to uniquely identify each device connected to the network, enabling communication between them.
IP addresses are divided into two main categories:
- IPv4: A 32-bit address represented in dotted decimal notation, e.g., 192.168.1.1.
- IPv6: A 128-bit address using hexadecimal notation, e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
The diagram likely utilizes IPv4 addresses, as it represents a traditional network setup. However, the use of IPv6 addresses is becoming increasingly common for modern networks.
Routing Protocols
Routing protocols play a crucial role in determining the optimal paths for data transmission between network devices. They allow routers to exchange information about network topology and connectivity, enabling them to build routing tables that map destinations to the most efficient routes.
Routing protocols can be categorized into two main types:
- Distance-vector routing protocols: These protocols rely on each router sharing its entire routing table with its neighbors. Routers then calculate the shortest path to a destination based on the information received from their neighbors. Examples include RIP (Routing Information Protocol)and IGRP (Interior Gateway Routing Protocol).
- Link-state routing protocols: These protocols involve each router broadcasting its local network information to all other routers on the network. Routers then construct a complete map of the network topology and calculate the shortest paths to all destinations. Examples include OSPF (Open Shortest Path First)and IS-IS (Intermediate System to Intermediate System).
Routing Algorithm Examples
Routing algorithms are used by routing protocols to determine the optimal path for data transmission.
- Dijkstra’s Algorithm: This algorithm is widely used in link-state routing protocols. It calculates the shortest path between two nodes in a graph, considering the weight of each edge (representing network latency or cost).
- Bellman-Ford Algorithm: This algorithm is used in distance-vector routing protocols. It iteratively updates the distance estimates to each destination based on the information received from neighboring routers.
In the 192-97 LT1 diagram, the specific routing protocols and algorithms employed would depend on the network design and configuration. For example, if the network is relatively small and simple, a distance-vector protocol like RIP might be sufficient. However, for larger and more complex networks, a link-state protocol like OSPF might be more suitable.
Data Transmission Process
The data transmission process in the 192-97 LT1 diagram involves the movement of data from a source device to a destination device through a series of network layers. Each layer adds its own header information to the data, encapsulating it for transmission.
This process ensures that the data is properly formatted and delivered to the correct recipient.
Data Encapsulation and Decapsulation
Data encapsulation and decapsulation are essential processes in data transmission. Encapsulation refers to the process of adding header information to the data at each layer. This header information contains control information specific to that layer, such as addressing, routing, and error detection.
Decapsulation is the reverse process, where the header information is removed at each layer as the data travels from the source to the destination.
- Application Layer:The application layer encapsulates the data with application-specific information, such as the protocol used and the type of data being transmitted. This layer is responsible for providing services to the user applications, such as email, web browsing, and file transfer.
- Transport Layer:The transport layer adds its own header, which includes information about the port number, sequence number, and checksum. This layer is responsible for segmenting the data into smaller packets and ensuring reliable data delivery between applications on different hosts.
- Network Layer:The network layer adds a header that includes the source and destination IP addresses. This layer is responsible for routing the data packets across the network.
- Data Link Layer:The data link layer adds a header that includes the MAC addresses of the source and destination devices. This layer is responsible for error detection and correction at the physical level.
- Physical Layer:The physical layer transmits the data bits over the physical medium, such as a cable or wireless signal.
Error Detection and Correction Mechanisms
Error detection and correction mechanisms are crucial for ensuring reliable data delivery. These mechanisms help to detect and correct errors that may occur during data transmission.
- Checksum:A checksum is a simple error detection mechanism that calculates a value based on the data being transmitted. This value is included in the data packet, and the receiver can calculate the checksum again to verify the integrity of the data.
If the checksums do not match, the receiver knows that an error has occurred.
- Parity Check:A parity check is another simple error detection mechanism that adds an extra bit to the data stream. This bit is set to 0 or 1 based on the number of 1 bits in the data stream. The receiver can then check the parity bit to detect if any errors have occurred.
- Cyclic Redundancy Check (CRC):CRC is a more sophisticated error detection mechanism that uses a polynomial division to calculate a checksum. This checksum is more robust than a simple checksum and can detect a wider range of errors.
- Forward Error Correction (FEC):FEC is a technique that adds redundant data to the data stream. This redundant data can be used to correct errors that occur during transmission. FEC is typically used in applications where the channel is noisy or unreliable.
Network Security Considerations

The 192-97 LT1 diagram, while representing a simplified network topology, highlights potential vulnerabilities that require attention. It is crucial to understand the security threats and implement appropriate measures to safeguard the network and its data.
Identifying Security Threats and Vulnerabilities
Security threats in a network like the 192-97 LT1 diagram can arise from various sources, including malicious actors, misconfigurations, and unintentional user actions. These threats can exploit vulnerabilities in the network infrastructure, protocols, and applications, potentially leading to data breaches, system failures, and service disruptions.
- Unauthorized Access:Unsecured network access points, such as open Wi-Fi networks or poorly configured routers, can allow unauthorized individuals to gain access to the network and its resources.
- Data Interception:Network traffic, including sensitive data like login credentials and financial information, can be intercepted by attackers using techniques like packet sniffing and man-in-the-middle attacks.
- Malware Infections:Malicious software, such as viruses, worms, and Trojans, can infiltrate the network through various means, including email attachments, infected websites, and vulnerable software.
- Denial-of-Service Attacks:Attackers can overwhelm network resources with excessive traffic, making the network unavailable to legitimate users.
- Misconfigurations:Incorrectly configured network devices, firewalls, and security protocols can create vulnerabilities that attackers can exploit.
Implementing Security Protocols and Measures
To mitigate these security risks, a multi-layered approach is essential. This involves implementing security protocols, deploying security tools, and adopting best practices to enhance network security.
- Firewalls:Firewalls act as a barrier between the network and the outside world, blocking unauthorized access and malicious traffic. They can be implemented at the network perimeter, individual devices, or within applications.
- Intrusion Detection and Prevention Systems (IDS/IPS):These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and blocking malicious traffic.
- Virtual Private Networks (VPNs):VPNs encrypt network traffic, protecting data from interception and unauthorized access. They are particularly useful for remote users accessing the network over public Wi-Fi connections.
- Strong Passwords and Authentication:Implementing strong password policies and multi-factor authentication can significantly reduce the risk of unauthorized access.
- Regular Security Updates:Keeping operating systems, software, and firmware up-to-date is crucial for patching vulnerabilities and preventing attackers from exploiting known weaknesses.
Security Best Practices
- Network Segmentation:Dividing the network into smaller, isolated segments can limit the impact of security breaches. This principle helps contain the spread of malware and prevents attackers from gaining access to sensitive data.
- Least Privilege Principle:Users and applications should only have access to the resources they need to perform their tasks. This principle helps minimize the potential damage caused by malicious actors or accidental misuse.
- Data Encryption:Encrypting sensitive data at rest and in transit can protect it from unauthorized access, even if the network is compromised.
- Regular Security Audits:Conducting regular security audits can identify vulnerabilities and misconfigurations that may have been overlooked.
- Security Awareness Training:Educating users about common security threats and best practices can help reduce the risk of human error and social engineering attacks.
Network Performance and Optimization
Network performance is a crucial aspect of any network, especially in the context of the 192-97 LT1 diagram. Understanding the factors that influence performance and implementing optimization techniques are essential for ensuring smooth and efficient data transmission.
Factors Influencing Network Performance
Network performance can be affected by various factors, including:
- Bandwidth:The amount of data that can be transmitted over a network connection within a given time. Insufficient bandwidth can lead to slow data transfer speeds and network congestion.
- Latency:The time delay between sending a data packet and receiving a response. High latency can result in slow response times and a laggy user experience.
- Jitter:Variations in latency, which can cause packet loss and disrupt data streams, leading to audio and video interruptions.
- Packet Loss:When data packets fail to reach their destination, resulting in lost information and requiring retransmission, which further impacts performance.
- Network Congestion:When too much data is being transmitted over a network connection, leading to delays and packet loss.
- Hardware Limitations:The capacity and performance of network devices, such as routers and switches, can impact overall network performance.
- Software Configuration:Network settings, such as routing protocols and firewall configurations, can influence network performance.
- Security Measures:Security protocols, like firewalls and intrusion detection systems, can introduce latency and overhead, impacting network performance.
- Application Demands:The type and volume of data transmitted by applications can significantly affect network performance.
Techniques and Strategies for Network Optimization
Network optimization involves implementing techniques and strategies to enhance network performance and efficiency. Some common approaches include:
- Bandwidth Management:Controlling and prioritizing network traffic to ensure that critical applications receive sufficient bandwidth, while less important traffic is throttled or delayed. Techniques include Quality of Service (QoS) and traffic shaping.
- Traffic Shaping:Managing the rate and timing of data packets to ensure smooth and consistent network flow. This involves smoothing out bursts of traffic and prioritizing important data packets.
- Network Segmentation:Dividing the network into smaller, isolated segments to reduce congestion and improve security. This can also help prioritize traffic within specific segments.
- Network Monitoring and Analysis:Regularly monitoring network performance using tools and technologies to identify bottlenecks, anomalies, and potential issues. This allows for proactive troubleshooting and optimization.
- Hardware Upgrades:Upgrading network devices, such as routers and switches, with higher capacity and performance can improve network throughput and reduce latency.
- Software Optimization:Fine-tuning network settings and configurations to optimize performance. This includes adjusting routing protocols, firewall settings, and other parameters.
- Application Optimization:Optimizing applications to reduce their network usage and improve efficiency. This may involve using compression techniques, minimizing data transfers, and optimizing application protocols.
Tools and Technologies for Network Monitoring and Analysis
Several tools and technologies are available for network monitoring and analysis, providing valuable insights into network performance and identifying areas for optimization. Examples include:
- Network Performance Monitors (NPMs):Software applications that collect and analyze network data, providing real-time performance metrics and historical trends. Popular NPMs include SolarWinds Network Performance Monitor, PRTG Network Monitor, and ManageEngine OpManager.
- Network Analyzers:Tools that capture and analyze network traffic, providing detailed information about data packets, protocols, and network performance. Examples include Wireshark, tcpdump, and Network Traffic Analyzer (NTA) from Cisco.
- Network Management Systems (NMS):Comprehensive platforms that manage and monitor various network devices, including routers, switches, and firewalls, providing centralized control and performance monitoring.
- Packet Sniffers:Tools that capture and analyze network traffic, providing insights into data flow, protocol usage, and potential security threats. Popular packet sniffers include Wireshark and tcpdump.
- Performance Monitoring Tools:Specialized tools designed to monitor and analyze the performance of specific applications or services, providing insights into their resource utilization and potential bottlenecks.
Real-World Applications
The 192-97 LT1 diagram, while a theoretical model, finds practical applications in various real-world scenarios, particularly in network design, troubleshooting, and security analysis. Understanding how this diagram translates into real-world scenarios provides valuable insights into its impact on network communication across different industries.
Network Design and Planning
The 192-97 LT1 diagram serves as a foundational tool in network design and planning, enabling network engineers to visualize and understand the different layers involved in network communication. It aids in:* Defining Network Architecture:The diagram provides a clear framework for defining the architecture of a network, outlining the various layers and their functionalities.
This helps in identifying the components needed for specific network applications.
Choosing Appropriate Protocols
By understanding the functions of each layer, network designers can choose the most appropriate protocols for specific network tasks, ensuring optimal performance and compatibility.
Addressing Network Requirements
The diagram assists in understanding the network requirements of different applications and ensuring the network infrastructure can support them effectively.
Network Troubleshooting
The 192-97 LT1 diagram proves instrumental in network troubleshooting, providing a structured approach to pinpointing the source of network problems. It allows network administrators to:* Isolate Network Issues:By analyzing the different layers of the network, administrators can isolate the layer responsible for the issue, enabling them to focus their troubleshooting efforts.
Identify Potential Causes
The diagram helps identify potential causes of network problems by understanding the functionalities and interactions of each layer.
Develop Effective Solutions
The knowledge gained from the diagram guides the development of effective solutions to network issues, ensuring the network’s stability and performance.
Network Security Analysis
The 192-97 LT1 diagram is essential in network security analysis, helping security professionals understand how attacks can exploit vulnerabilities at different layers. It enables them to:* Identify Security Threats:By analyzing the different layers, security professionals can identify potential attack vectors and vulnerabilities that attackers might exploit.
Implement Effective Security Measures
The diagram provides a framework for implementing effective security measures at different layers, ensuring a layered approach to network security.
Analyze Security Incidents
The diagram assists in analyzing security incidents, understanding the impact of the attack on different network layers and developing appropriate response strategies.
Network Performance Optimization, 192-97 lt1 diagram
The 192-97 LT1 diagram plays a crucial role in network performance optimization, providing insights into network bottlenecks and enabling administrators to make informed decisions to improve network efficiency. It allows them to:* Identify Performance Bottlenecks:By analyzing the traffic flow at different layers, administrators can identify bottlenecks that hinder network performance.
Optimize Network Configuration
The diagram guides network configuration optimization, ensuring efficient resource allocation and optimal data flow across the network.
Implement Performance Monitoring Tools
The understanding of network layers enables the effective implementation of performance monitoring tools, providing real-time insights into network performance and potential issues.
Future Trends and Developments
The 192-97 LT1 diagram, while providing a comprehensive overview of network communication, is constantly evolving as technology advances. Emerging trends and advancements in network communication are influencing the diagram, leading to potential changes and adaptations. This section explores these trends and provides insights into the future of network communication and its impact on the diagram.
The Rise of 5G and Beyond
The advent of 5G technology has revolutionized wireless communication, offering significantly higher speeds, lower latency, and greater capacity. 5G networks are designed to handle the increasing demand for data and support new applications such as the Internet of Things (IoT), augmented reality (AR), and virtual reality (VR).
This advancement will likely impact the 192-97 LT1 diagram in several ways:
- Enhanced Network Performance:5G’s improved speed and low latency will necessitate adjustments to the diagram, particularly in the physical layer, where data transmission rates and error correction mechanisms need to be updated to accommodate the higher bandwidth.
- Increased Network Complexity:5G networks are more complex than previous generations, requiring new protocols and functionalities for network slicing, edge computing, and device management. The diagram will need to incorporate these new elements to reflect the evolving network architecture.
- New Applications and Services:The rise of 5G will enable the development of new applications and services that were previously impossible. The diagram will need to be adaptable to incorporate these new services, such as real-time data analytics, cloud gaming, and autonomous vehicle communication.
The Evolution of Cloud Computing
Cloud computing has become ubiquitous, offering a flexible and scalable platform for businesses and individuals. Cloud services are constantly evolving, with new technologies and advancements emerging regularly. The impact of cloud computing on the 192-97 LT1 diagram can be summarized as follows:
- Shift in Network Traffic Patterns:The increasing use of cloud services will lead to a shift in network traffic patterns, with more data flowing between data centers and users. This will necessitate adjustments to the diagram, particularly in the transport layer, where protocols like TCP and UDP need to be optimized for cloud-based communication.
- New Security Challenges:Cloud computing introduces new security challenges, such as data breaches and unauthorized access. The diagram will need to incorporate security considerations, such as encryption and authentication mechanisms, to ensure data integrity and confidentiality.
- Software-Defined Networking (SDN):Cloud computing has driven the adoption of SDN, which allows for greater flexibility and control over network infrastructure. The diagram will need to reflect this shift, incorporating elements of SDN, such as centralized control planes and programmability.
The Rise of the Internet of Things (IoT)
The IoT is a network of interconnected devices that collect and exchange data. The proliferation of IoT devices is driving significant growth in network traffic and demanding new network capabilities. The impact of IoT on the 192-97 LT1 diagram is evident in the following:
- Increased Data Volume:The vast number of IoT devices will generate massive amounts of data, necessitating adjustments to the diagram to handle the increased data volume. This includes optimizing network protocols, such as TCP and UDP, for efficient data transmission.
- New Communication Protocols:The IoT requires specialized communication protocols for device discovery, data exchange, and security. The diagram will need to incorporate these new protocols, such as MQTT and CoAP, to reflect the specific requirements of IoT communication.
- Edge Computing:To handle the real-time processing of data generated by IoT devices, edge computing is becoming increasingly important. The diagram will need to incorporate edge computing concepts, such as distributed processing and data caching, to optimize performance and reduce latency.
Artificial Intelligence (AI) and Machine Learning (ML) in Networking
AI and ML are transforming various industries, including networking. AI and ML are being used to optimize network performance, improve security, and automate network management. The implications for the 192-97 LT1 diagram are significant:
- Intelligent Routing and Traffic Management:AI and ML can be used to optimize routing paths and manage network traffic in real time, based on network conditions and user demands. This will lead to improvements in network performance and efficiency.
- Enhanced Security:AI and ML algorithms can be used to detect and prevent network security threats, such as malware attacks and data breaches. The diagram will need to incorporate these AI-powered security mechanisms to enhance network resilience.
- Automated Network Management:AI and ML can automate various network management tasks, such as network configuration, troubleshooting, and capacity planning. This will free up network administrators to focus on more strategic initiatives.
FAQ Insights
What are the key benefits of using the 192-97 LT1 diagram?
The 192-97 LT1 diagram offers several benefits, including:
- Simplified understanding of network communication
- Standardized framework for network analysis and troubleshooting
- Improved network security by identifying potential vulnerabilities
- Enhanced network performance through optimized communication processes
How does the 192-97 LT1 diagram relate to real-world applications?
The 192-97 LT1 diagram is applied in various real-world scenarios, including:
- Internet communication
- Corporate intranets
- Wireless networks
- Cloud computing